Introduction to firewall
A firewall is a network security system that monitors incoming and outgoing network traffic and allows or blocks the data packets based on a set of security rules that are predefined in the system. It acts as a barrier between internal and external sources such as the internet and blocks malicious traffic.
A firewall can be categorized into –
Network firewall
A network firewall filters traffic between two or more networks and runs on network hardware.
Host-based firewall
A host-based firewall runs on the host computer and controls the network traffic in and out of that system.
How does a firewall work?
Firewall carefully analyze the traffic which is coming from different sources and filter the unsecured and suspicious one so that the host computer can be prevented from the external attack.
An external device establishes the connection with a computer and exchanges the information through an entry point on that computer these entry points are known as port.
For example – Suppose a system installed with ssh client want to establish the connection with an ssh server. Then first it will have to make a connection request to the server, the firewall on the server will analyze it based on the predefined rules. If it finds it a trusted source then it will be allowed to get connected over port 22 otherwise it gets rejected.
Uncomplicated Firewall(ufw)
The uncomplicated firewall is the default firewall configuration tool for Ubuntu, Linux Mint, and such other Linux distributions. It provides a user-friendly and easy way to create an iptable firewall configuration.
The ufw does not provide complete firewall functionality but instead, it provides an easy way to add or remove simple rules. It is mainly used for host-based firewalls.
How to use ufw
By default, ufw is disabled so if you want to use it, first you will have to enable it.
1. You can check the status of the firewall that will be either active or inactive –
sudo ufw status
2. Enable it by using the given command-
sudo ufw enable
3. To open a port lets say 22 (port used by ssh) use the given command
sudo ufw allow 22
4. Similarly to close an opened port use the following command
sudo ufw deny 22
5. The firewall rules also can be added using a numbered format
sudo ufw insert 1 allow 80
6. To remove a rule, you should use the given command
sudo ufw delete deny 22
7. Using –dry-run option with ufw command will output resulting rules but not apply them. For example –
sudo ufw --dry-run allow http
The above command when executed will display some rules and filters that get applied if opening the HTTP port.
8. ufw can be disabled by using
sudo ufw disable
Applications that open port can include an ufw profile. These profiles are kept in /etc/ufw/applications.d and can be edited if the default port has been changed. A profile contains the details of the port used by the application that opened it and it is needed for the application to function properly.
9. To view which application has installed a profile use the following command
sudo ufw app list
 Now this command will display the list of available applications.
Now this command will display the list of available applications.
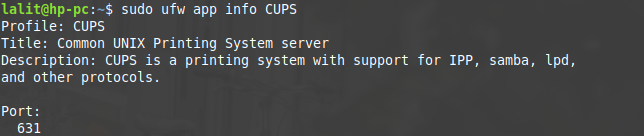
10. And to view details of port, protocols used by the application use the given command
sudo ufw app info application_name
GUI tools to configure a firewall
You can make using this handy firewall even easier by using GUI tools that are available for it. Gufw is one of the most popular GUI front ends available for ufw.
By using Gufw you can easily add or remove a rule, you can create a profile for home, office, or the public.
In some Linux distributions, it comes preinstalled, but if you do not have it in your system you can install it by using the given command.
In debian based Linux distributions, use-
sudo apt install gufw

As you can see above it is the GUI interface of Gufw application.
Now I hope this might give you some insight into the topic. If you want to say something about this you can write to us in the comments below.