AppArmor is a Linux security module that allows a system administrator to control or restrict a program’s capabilities using its profiles, In other words, it uses application profiles to determine what files and permissions that application needs.
It proactively protects the operating system and applications from internal or external threats and prevents both known and unknown flaws in applications from being exploited.
AppArmor supplements Unix Discretionary Access Control (DAC) model by providing Mandatory Access Control. It comes default in various Linux distributions such as Ubuntu, OpenSUSE, Debian, etc. It is similar to SELinux a security module in Redhat and Fedora Linux.
In this article, I will discuss AppArmor its installation and usage on a Linux system.
How to install AppArmor in Linux
As discussed earlier by default AppAromor comes integrated with the kernel in various distributions so you do not need to install it explicitly.
You can check the status of AppArmor on your system by using –
aa-status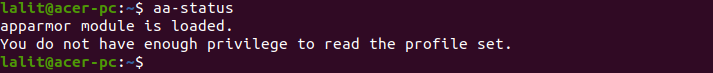
You can read the profile set by running this command as root or with superuser privileges.
Some packages will install their own profiles or properties and more can be found in apparmor-profiles package. You can use the following command to install this package on your system –
sudo apt install apparmor-profilesThe commands for configuring AppArmor are contained in apparmor-utils packages. You can install this package by using –
sudo apt install apparmor-utilsAppArmor profiles
AppArmor profiles are text files located in /etc/apparmor.d directory. These are named after the full path to the executable they profile, replacing ‘/’ with ‘.’. For example /etc/apparmor.d/bin.ping is the profile for ping in /bin.
Two main types of rules used in profiles are –
Path entries – It determines what files an application can access.
Capability entries – It determines what privileges a confined process is allowed to use.
The AppArmor profiles have two modes of execution –
Complaining/ Learning mode -Profile violations are permitted and logged it is useful for testing and developing new profiles.
Enforced/Confined mode – Enforces profile policy as well as logging the violation.
You can view current profiles set on your system by using the given command –
sudo aa-status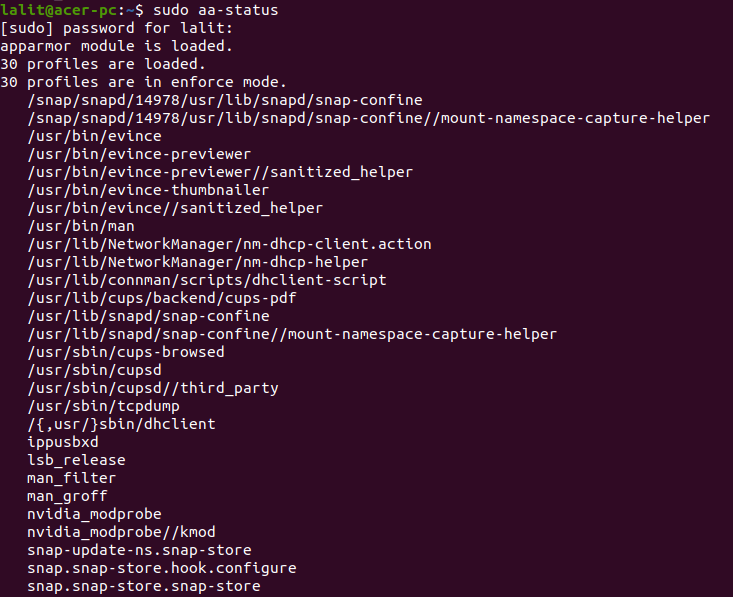
How to use AppArmor
You can install the apparmor-utils package which contains various command-line utilities for working with AppArmor. Some of them are discussed below.
To view the current status of the AppArmor profile –
sudo apparmor_statusTo place a profile in complain mode use –
sudo aa-complain /path/to/binIf you want to place a profile in enforce mode then use –
sudo aa-enforce /path/to/binYou can reload all profiles by using –
sudo systemctl reload apparmor.serviceThe apparmor_parser is used to load a profile into the kernel, you can use the following command to reload a profile –
sudo apparmor_parser -r /etc/apparmor.d/profile.nameTo disable a profile you can use –
sudo ln -s /etc/apparmor.d/profile.name /etc/apparmor.d/disable/
sudo apparmor_parser -R /etc/apparmor.d/profile.nameFor more details of how to use AppArmor commands, you can view its official documentation.
Conclusion
So in this article, we have explained what is the AppArmor and how to use it in a Linux system. Now if you have a query then write us in the comments below.